A Peek into Our Webinar: Applying Zero Trust Security to Sensitive Healthcare IoT Environments

Attacks on healthcare facilities are on the rise. Millions of patient records have been exposed, hospitals have been shut down, and tens of thousands of critical connected Healthcare IoT devices have been compromised.
Here’s a sneak peek into Cynerio’s webinar with Carahsoft on how hospitals and other healthcare organizations can safely apply the Zero Trust framework to their networks to protect themselves from every kind of threat, from device-level vulnerabilities to targeted ransomware attacks.
Know What Needs Protection
Medical/IoMT devices, Enterprise IoT, and OT systems pose the biggest threat to hospital networks and have a major impact on patient safety, data confidentiality, and business continuity.
What Is Zero Trust?
As networks have become more complex and decentralized in recent years, the attack surface of Healthcare IoT networks has expanded, increasing the need for more security and segmentation.
The Zero Trust concept operates on the premise that nothing should be trusted inside or outside its perimeters and boils down to “never trust, always verify”. There should be no immediate trust between any two entities on the network, and every connection must be authenticated and verified on an individual basis.

Why Is Healthcare IoT So Vulnerable?
While the Zero Trust framework answers the security needs of most industries, applying it to healthcare ecosystems can be extremely challenging.
Healthcare IoT devices make easy targets for threat actors because of their inherent vulnerabilities, from outdated operating systems and firmware, unmanaged vendor access, misconfigurations, and open ports, to weak and/or default passwords that allow access to almost anyone.
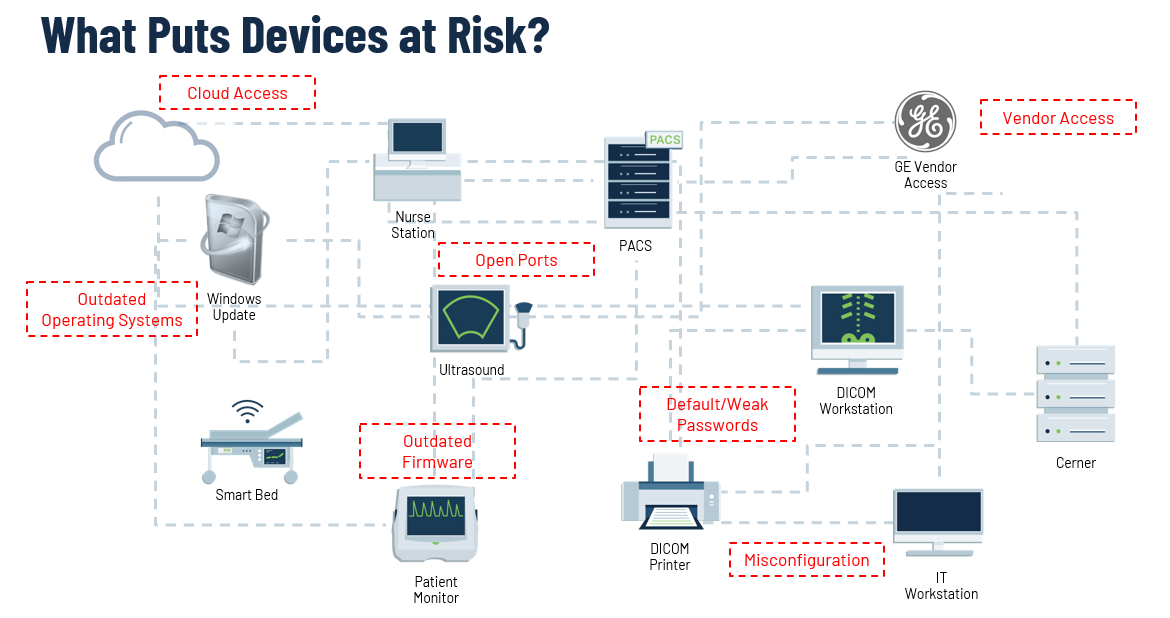
Healthcare-safe Zero Trust must be used as a guiding security framework that takes these critical connections into account and builds policy around them that simultaneously preserves function and clinical workflow while blocking all unnecessary connections. The best way to understand how to apply Zero Trust to Healthcare IoT is through real-world examples like ransomware attacks and managing vendor access.
Use Case 1: Preventing Ransomware Attacks
Ransomware is today’s biggest threat to healthcare. In 2020 alone, ransomware has been responsible for the 3-week shutdown of 400 UHS facilities across the US, a return to pen-and-paper following the shutdown of all PCs at France’s University Hospital Center, a system-wide outage at UVM, and the death of a patient at Dusseldorf University hospital in Germany.
Just in Q3 2020, there was a 50% rise in the daily average of ransomware attacks on US healthcare systems.
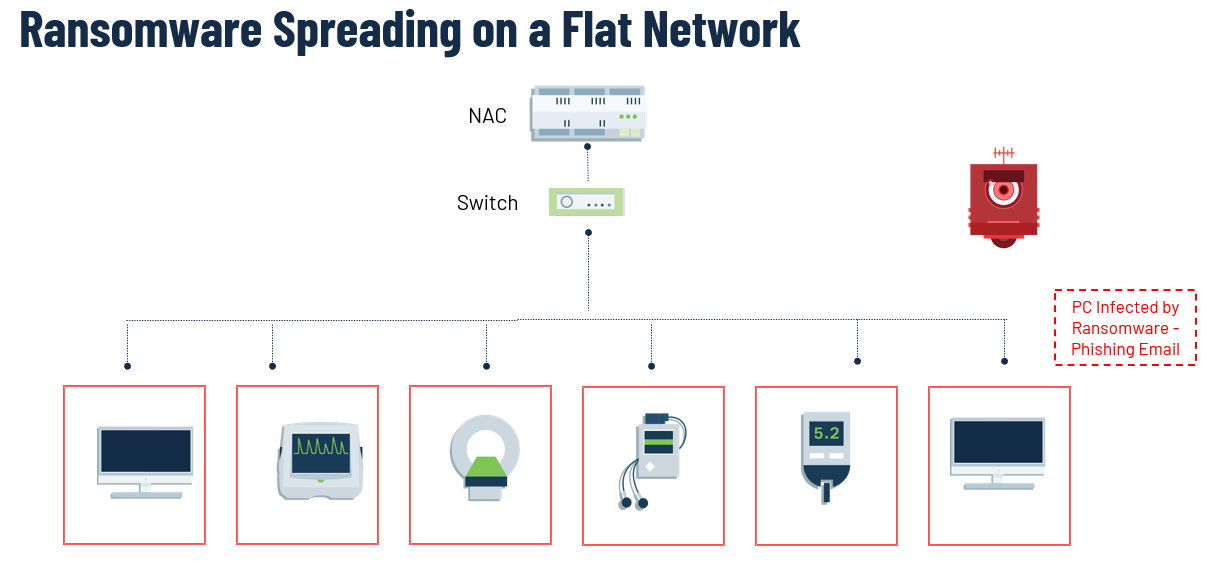
How Does Ransomware Spread?
Ransomware usually enters the network by infecting a PC after gaining entry through a phishing email. On a flat network, without segmentation, the ransomware can quickly spread from one device to another, because the infected PC is allowed to communicate with every other device on the network.
To illustrate how fast this can happen, Ryuk ransomware can infect and encrypt an entire network in just 5 hours. It’s no surprise then, that Ryuk ransomware is responsible for one-third of all cyber attacks in 2020.
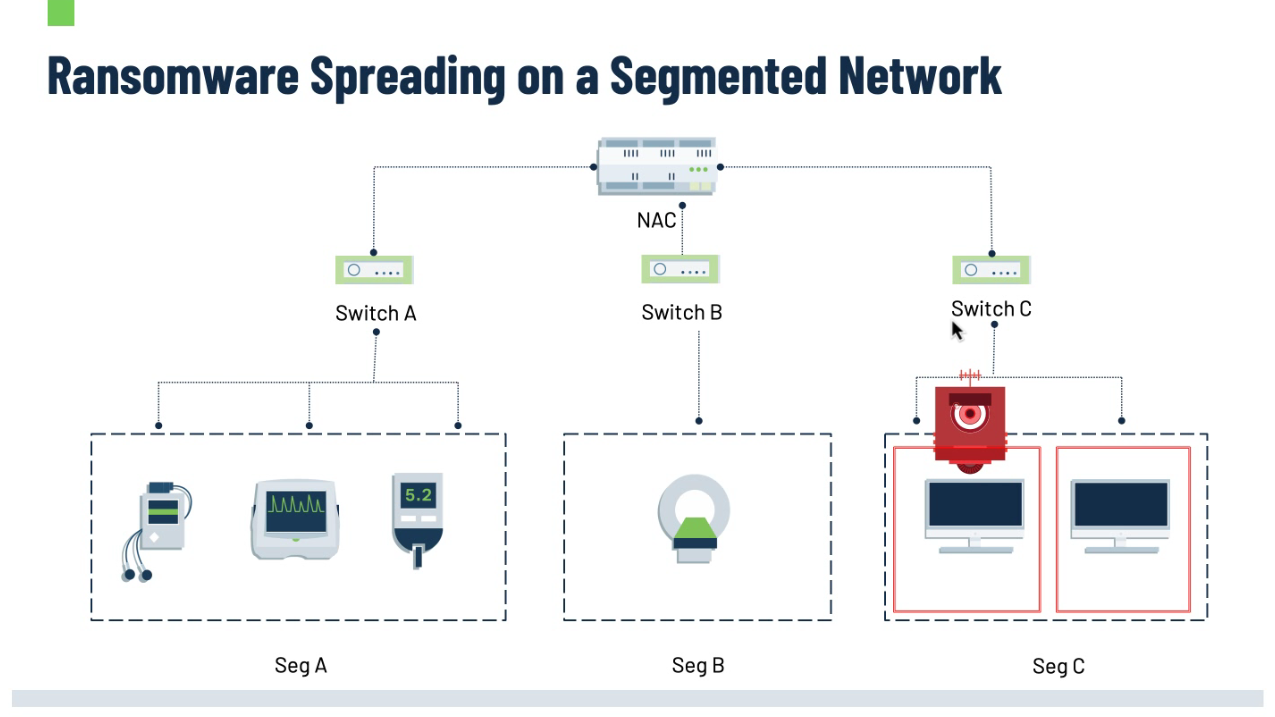
Preventing the Spread of Ransomware with Segmentation
The impact of ransomware attacks can be minimized by segmenting networks using healthcare-safe Zero Trust segmentation policies:
- North-South segmentation will prevent ransomware and other malware from penetrating the network.
- East-West segmentation will limit the ability for infections to move laterally by decreasing the attack surface and isolating groups of devices. It will prevent devices from communicating with each other and will keep infections confined to a specific segment, minimizing the effect of an attack.
Why Is Segmentation Difficult to Implement?
Traditional security infrastructures don’t provide Healthcare IoT asset visibility, there’s a fear of medical service disruption, and acute limits to available manpower.
Cynerio helps healthcare facilities overcome these obstacles by providing full visibility with clinically-enriched, ongoing mapping and inventory. Our Virtual Segmentation tackles further challenges and expedites safe segmentation projects by allowing hospitals and clinics to:
- Automate custom policies
- Test policies for safety
- Tune up policies
- Complete projects within weeks
Preventing the Spread of Ransomware by Quarantining Devices
If ransomware successfully infects a mission-critical device, disconnecting isn’t an option because patients’ lives depend on it. In cases like this, hospitals can use a laser-focused Zero Trust approach to mitigate the threat with Quarantine. Quarantine will:
- Keep devices functional
- Avoid a complete shutdown by preventing spread
- Enable device disconnects for patching and updates during downtime
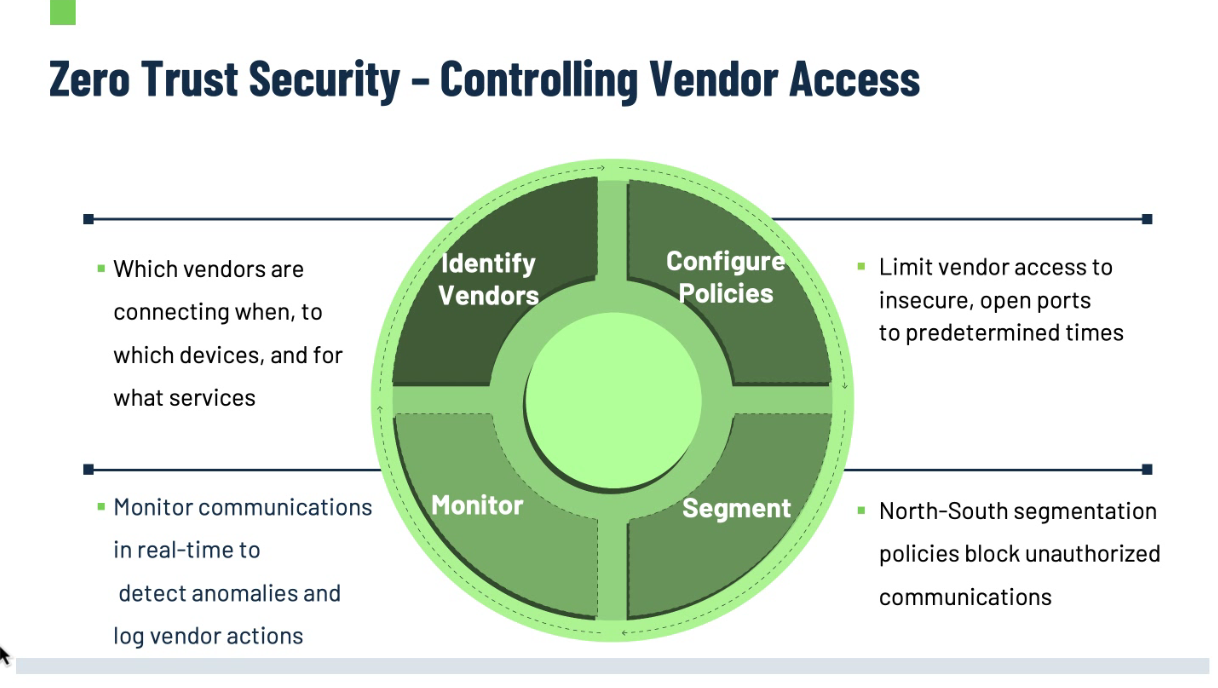
Use Case 2: Controlling 3rd Party Vendor Access
Connections to devices for routine maintenance services are often required by vendors, but these unmanaged connections are also a threat vector:
- Hospitals have no control over vendor networks
- Vendor communications aren’t always limited to authorized devices
- Standard IoT and IT security tools can’t be applied
This threat can be mitigated by gaining control over vendor connections by applying Zero Trust policies.
To learn more about how to apply a Zero Trust security policy to your healthcare IT network, watch the full webinar.
.webp)

.png)




